Ransomware: Backup or Pay up!
I've blogged before about increasing security threats. For the most part, virus and worm attacks have been a nuisance, and readily fixed by an expert even without a backup, but now a much more dangerous worm has emerged. I know of a couple of local Illinois companies who have been hit. To bring this home, about 20% of businesses will get hit with some kind of serious virus. If they are not backed up and secure, 60% of them will go out of business within six months of the attack.
In September of 2013, a new ransomware threat emerged primarily attacking computers with Windows operating systems. It is called CryptoLocker and it is different from earlier ransomware in that it does not just freeze your computer screen, like the old RansomLock did, it actually encrypts your data files and the only people that have the decryption key are the cyber criminals that control CryptoLocker!
CryptoLocker is a Trojan Horse Malware. It is a form of ransomware usually disguised as an email attachment. We have however, also seen it as a “trust us, we can fix everything” link at the bottom of emails from, what looks like, a trusted source. The cyber criminals are very good at making their spam emails look just like the emails from trusted sources.
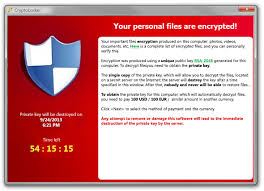
When you open the attachment or click on the link you activate malware that encrypts your data files with a powerful 2048 bit RSA key pair encryption code. There are no flaws to attack and reveal the decryption key, neither is brute force possible. The only copy of the private decryption key is in the possession of the malware operator(s). It will display a message on your screen offering to decrypt your files if you pay 0.5 -1.0 bitcoin or $300 US or 300 Euro within 72 hours using an anonymous pre-paid voucher, like a pre-paid Visa gift card. About 3% pay up. If the 72 hours elapses, these criminals have an online service that claims to allow you to decrypt your files by uploading one of your encrypted files to their site, as a sample of the encryption, and within 24 hours they will find the correct decryption key and send it pre-loaded to you for a much HIGHER PRICE! We are talking 10 bitcoin or over $1500.00 US and the price just keeps going up! The nasty little Trojan also tries to delete the Windows shadow copy backup before it encrypts your files, making it much more difficult for those without cloud backup resources to restore their data files. A large number of data files are attacked, but some of the most prevalent are Microsoft Office, OpenDocument, pictures and AutoCAD files. The only good thing about this worm is that it doesn't self replicate and infect other computers like a virus. Each CryptoLocker victim had to trigger the worm manually (usually by clicking a link on the internet).
Of course, there is a way to defeat this. These Cyber criminals are counting upon you, the user, NOT having a valid backup of your files. The defeat of CryptoLocker is to have a valid backup from which you can restore your files. Something like the award winning Brella backup from PC Methods would do very nicely. Other simple, common sense security is to NEVER OPEN SPAM/JUNK EMAIL! What are YOU doing opening an attachment on a piece of junk email? We do not care what marvelous, magical goodies they are offering to you, there is a REASON WHY it is in the spam/junk folder! DO NOT OPEN IT!!! If you have opened an email from a source you trust that contains some kind of warning and, at the bottom, there is a “click here and fix everything” link, please question that link and do not click on it!
One of the anti-viral labs has created a DNS sinkhole to try to capture some of the domain names these criminals use for CryptoLocker. The problem is this nasty Trojan can generate millions of new domain names per day. Symantec has some good protection from this because Symantec questions the authority and reputation of everything all of the time. Amazingly, it does so without slowing the PC down or being unduly intrusive. Symantec also has an article out entitled “Recovering RansomLocked Files Using Built-In Windows Tools” that seems to be good.
The moral is to NOT open suspicious emails, especially from the spam/junk folder…to NEVER open an attachment on an email from the spam/junk folder…to QUESTION suspicious links on emails that look like they have come from a trusted source…and to HAVE a valid CLOUD BASED backup of your data files to use in the restoration of your computer. It is CryptoLocker today, tomorrow it will be something else…these criminals unfortunately never seem to run out of ideas. Let’s all hope the LAW catches up with the CryptoLocker operators someday.
Peter Heinicke
Chicago area ERP consultant and Managed Service Provider with over 45 years of experience in Sage 300, Sage Pro, Quickbooks ERP and other systems

