IT Support Blog
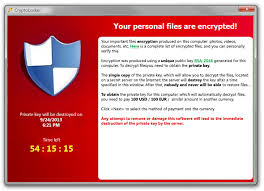
Tags: Backup, Backup to the cloud, Anti Virus, Symantec, Malware, Security Software, CryptoLocker, ransomware
How does one become CIPA compliant? If you just block a list of websites, it won't work because the bad guys are always jumping from url to url and it would be an impossible chore for one person to scan the net for all sites of a banned category. So, you go out and buy a filtering and/or blocking device that plugs into the system between where your internet service enters the building and the first router in line after that. These usually (but not always) come with a subscription to monitor the incoming material and check it against a constantly updated list of banned websites. WebSense will sell you a server, for several thousand dollars or more, complete with custom CIPA compliant programming for your particular school or library, which includes the subscription. Sounds ok, right? Surprise, you are still not CIPA compliant! Yes, you have stopped all of the incoming questionable material and have severely restricted the kids’ access to Facebook and other social media while at school. At the same time you have restricted You Tube, but can still use it for selected very good and educational videos on You Tube. But YOU ARE STILL NOT CIPA COMPLIANT!
Tags: Blogging, Blog, Web Content, Symantec, Security Software, Website Traffic
PC Methods offers a five block support offering for our IT clients. Not all clients choose to take advantage of all five blocks, but they are there if you want the best possible combination of value and service. The blocks are: Project Work, Centralized Services, Network Administration, Virtual CIO, and Support. These are the product offerings that clients should look for when selecting the best possible IT business partner.
Tags: IT services, Disaster Recovery, Backup, Backup to the cloud, Cloud Computing, Blogging, Blog, Anti Virus, Virus Removal, computer repair, Symantec, Malware, Security Software, Small Business, Sage 300 ERP
Tags: Anti Virus, Virus Removal, Symantec, Malware, Security Software